OnePacs Gateway Installation Guide (version 3.0+)
The following is a quick step-by-step guide to configuring a new installation of the OnePacs Gateway to transmit studies to OnePacs. The guide shows all the steps involved in configuring OnePacs to receive studies from one or more imaging facilities. Please refer to the more comprehensive Administrator’s Guide for further details.
Brief System Overview
In brief, DICOM studies are first transmitted from your PACS system(s) and/or modalities to a “Gateway” PC, which you supply and place on your local hospital network. When received at the Gateway PC, the studies are compressed, encrypted, and uploaded over the internet (via TLS/AES encrypted DICOM and HTTPS) to the OnePacs central server. On the central server, these received studies will be organized into a worklist which will be accessible to authorized users from any location on the internet. The Gateway PC will require a static local IP address on your local facility network such that studies can be pushed to it.
Please refer to the system diagram for an overview of the architecture of the OnePacs system.
Technical requirements
The following is a summary of the technical requirements of the OnePacs Gateway. For more information please see OnePacs Gateway Technical Requirements.
Hardware, software and bandwidth requirements:
| Computer | A physical server, PC, or virtual machine. |
| Operating System | Windows 11, or Windows Server 2016 through 2022 (64 bit) |
| Processor | High-end multicore modern processor required |
| Memory | 16 GB or more recommended (required w/ HL7 interface), 8 GB minimum |
| Disk Space | 2+ TB recommended, minimum 1 TB required |
| Internet Connectivity | Sufficient upload bandwidth required to handle the anticipated case transmission load. Generally, 20+ mbps upload bandwidth is recommended. Less than 5 mbps upload bandwidth is not supported. |
| Software Environment | The computer should be used exclusively for the purpose of running the OnePacs Gateway software. |
Network Requirements:
The OnePacs Gateway does not require a public IP address or any inbound ports to be opened in your organization's firewall. A static private IP address on a secure local area network is required to provide a fixed target for your DICOM devices to communicate with. Inbound DICOM traffic is received on the local network port 4104 (configurable), and the Gateway communicates with the OnePacs Cloud on a *.onepacs.com domain on port 443 using TLS. Please ensure your firewall allows this outgoing traffic.
Installation Requirements:
| User Account | A local Administrator Windows user account is required to perform the installation. It must be a local account - not a domain user. |
| AE Title | You must obtain a licensed AE title from OnePacs prior to installing the OnePacs Gateway as it will be required during the installation setup. |
| Host Name | The Windows computer name must not contain the underscore (_) character |
| Internet security permissions | Ensure internet security settings allow localhost applications - pgadmin opgateway |
| Whitelistings | Whitelist *.OnePacs.com, xonepacsdep-downloads.s3.amazonaws.com, and Amazon's us-east-01 IP range. |
Additional Requirements For Interfaces:
| Mirth Connect | https://www.nextgen.com/solutions/interoperability/mirth-integration-engine |
| Java | OpenJDK, Zulu, Etc. |
Security
The OnePacs license agreement requires physical access restrictions limiting physical access to the gateway computer to authorized personnel with a legitimate need to access the equipment and/or the use of whole hard disk encryption (e.g. BitLocker).
The OnePacs Gateway should not be configured to support storage of DICOM images from multiple unrelated organizations.
For additional security considerations please see OnePacs Gateway Technical Requirements.
Installation steps
Pre-Install Checklist
- You should already have a designated AE title for facility that the Gateway will be installed at. If not, please create a new facility or contact your group administrator to do so. Do not proceed with the Gateway installation unless you have an AE title for the facility.
- Ensure that the technical requirements and networking requirements described above are met. In particular, the PC must have a static local IP address on the local network.
- Verify that the Windows user account you're using is an administrator account on the local machine (not a domain user). The installation of the PostgreSQL service may fail otherwise.
- Create a system restore point before install if there is any doubt regarding conflicts caused by the prerequisite installations (Microsoft Visual C++ 2015-2019 x86 14.22.27821, PostgreSQL 17)
- If anti-virus is installed, it is a good idea to temporarily disable it before the install.
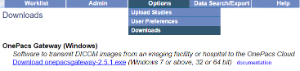
(1) Download the OnePacs Gateway
Log into OnePacs. Select the "Options" menu and choose the "Downloads" option. If your user account is authorized to download the OnePacs Gateway you will see it as an option on the downloads page.
Download the Windows executable for the OnePacs Gateway and save the file.
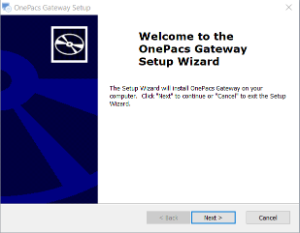
(2) Run the Installer
Remember to execute the installer only while logged in as a local Administrator. Run the installer by double clicking the file.
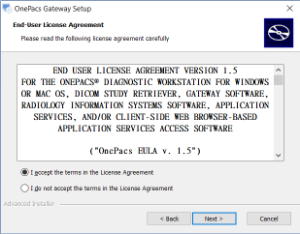
Click "Next" to proceed to the license agreement.
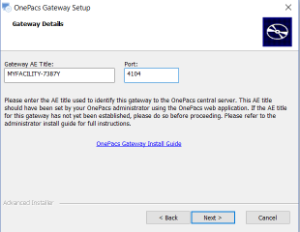
Read and agree to the license agreement. Then click "Next". This will bring you to the Gateway Details page.
Enter the AE title specific to your facility exactly as it was provided to you. You may change the DICOM port if necessary. OnePacs recommends using the default port of 4104 unless there is a specific reason to change it.
IMPORTANT The AE title must exactly match the configured AE title in OnePacs. This value is case sensitive.
Click "Next" to proceed to the "Lossy Compression" page.
Read the lossy compression disclaimer. Please note that you may change the compression rules after the installation completes. Click "Next" to continue.
When ready, click on "Install" to begin the installation.
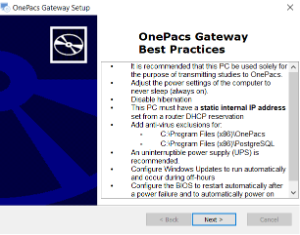
The installation will begin by installation prerequisite applications like Microsoft Visual C++ and the PostgreSQL database server. Once that completes, the installation of the OnePacs gateway will begin. Once the install completes you will see a "Best Practices" guide. Read this guide and ensure that all recommendations are considered.
Finally, click "Next" and "Finish" to complete the installation. Click "Yes" to reboot the PC after closing any other open applications.
(3) Set up Antivirus Exclusions
To optimize Gateway performance, and prevent conflicts with antivirus processes, please exclude the following directories from anti-virus scanning.
The Gateway will generally function normally even if this is not done, however, there is a potential for occasional transmission delays or errors related to anti-virus scanning, and it is recommended that this step be done.
C:\Program Files\OnePacs
C:\Program Files\PostgreSQL
(4) Connectivity Testing
Verify connectivity with the cloud by performing the connectivity testing step detailed on the user interface page.
(5) Configure your PACS and/or modalities to transmit to the Gateway PC
Configure the Gateway PC as a DICOM destination in your PACS and/or on your modalities. You can use the AE title GATEWAY for transmission; it is also possible to enter in the AE title which was set for the Gateway PC in step (2). The host name or address for transmission will be the static IP address assigned to the gateway, and the port for transmission is 4104 unless changed during the installation. We recommend sending uncompressed (ILE or ELE) unless the images are already lossy compressed (multi-frame US for example).
(6) Send test cases to OnePacs
Push test cases from your PACS and/or modalities to the Gateway PC, and log in to OnePacs and monitor the worklist for cases. Soon after pushing cases to the Gateway PC, you should see the cases begin to populate the OnePacs worklist.
(7) You’re done!
Should you experience any problem with the above setup, please contact OnePacs customer support for further assistance.
Summary of OnePacs Gateway Best Practices
The server/server environment on which the OnePacs Gateway software package runs is chosen by, configured, and maintained by the OnePacs client. Accordingly, it is the responsibility of the client to ensure the reliable and secure operation of the server.
OnePacs recommends the following as Best Practices in management of the server/server environment:
Function and reliability
• It is recommended that the OnePacs Gateway server be used solely for the purpose of transmitting studies to OnePacs, and facilitating OnePacs EMR integration. Installing any unrelated software packages increases the risk of issues and may impact performance.
• Adjust the power settings of the OS to never sleep (always on).
• Disable hibernation
• The gateway must have a static internal IP address set from a router DHCP reservation
• For performance purposes, it is best to add anti-virus exclusions for:
⁃ c:\onepacs
⁃ c:\Program Files\PostgreSQL
For physical machines (rather than virtual machines):
• Configure the BIOS to restart automatically after a power failure and to automatically power on shortly before normal usage begins
• An uninterruptible power supply (UPS) is recommended.
General security
The OnePacs Gateway stores sensitive information on the local server storage device(s), including Protected Health Information (PHI) as defined by the Health Insurance Portability and Accountability Act (HIPAA). Accordingly it should be treated with the same degree of security vigilance that would be appropriate for any other server at your facility containing similar information. The specific security measures and management procedures are at the discretion of the OnePacs client, however, OnePacs offers the following suggested best practices for consideration:
• Careful attention to physical security is important. Access to the room where the server is located (either a physical server, or the host machine in a VM setting) should be controlled, preferably by a method with user-specific tracking such as keycard access
• It is useful to engage physical lock devices on the hardware itself when available, in order to avoid theft of the device, and also to prevent opening of the device for the purpose of removing storage devices
• Bitlocker drive encryption with a Trusted Platform Module (TPM) is suggested for physical (non-VM) servers
• For physical (non-VM) devices, it may be useful to secure BIOS settings with a password, and disable booting from alternate media
• A Windows Server Core install is recommended. Unnecessary Windows services should be disabled
• Application of a Windows Security Baseline should be considered as a useful means of maintaining consistent security policies across various Windows installs within an organization
• Configure Windows Updates to run automatically during off-hours
• Disable automatic administrator login to the recovery console
• Windows Firewall should be configured to disallow incoming connections, other than for ports specifically opened by the installer(s) for the OnePacs software system components
• Provision logon accounts only to individuals with a genuine need to access the system
• For each user who needs access to the system, provision accounts with only the necessary privilege levels needed for that user to execute their responsibilities
• Regularly disable or delete accounts that are no longer needed, and regularly review and reduce privilege/permission levels that are no longer needed
• Mandate appropriate password complexity, and set other password related policies as considered best by your organization
• It is useful to check security and other logs regularly to screen for unauthorized or inappropriate access, including screening for authentication events, privilege escalation and usage, and other user access activity
• Regular system scans should be scheduled with the security software solution(s) of your choice
• Your network firewall and monitoring software will be of utility in monitoring for and blocking unauthorized access, as well as screening for anomalies such as spikes in traffic that could reflect data exfiltration
• Regular system backups will be useful in a recovery situation
Uninstalling and reinstalling the Gateway software
Uninstalling and reinstalling the Gateway software is not generally a useful troubleshooting step.
However, should you wish to do so, or if you are directed to do so by OnePacs technical support, the following steps are involved:
- Use the windows Add/Remove programs functionality to remove the software entitled “OnePacs Gateway”
- Reboot the computer
- Download the latest OnePacs Gateway installer and re-install the gateway software
Changing the AE title of the Gateway
If the AE title of the Gateway was entered incorrectly, or if you wish for any other reason to change the AE title of the gateway, please follow the steps on this page.